KeepassXC is a cross-platform password manager, I've been using it since it was originally just called KeePass with passwords in my database nearing ~15 years old. Very handy utility, has browser extensions, and so forth. The database itself is password encrypted so you can even just throw it on a cloud storage site to keep it backed up without worry for privacy.
KeepassXC also has a feature that allows you to generate 2FA codes directly from the application. After creating an entry, you can right click TOTP -> Setup TOTP to see this:
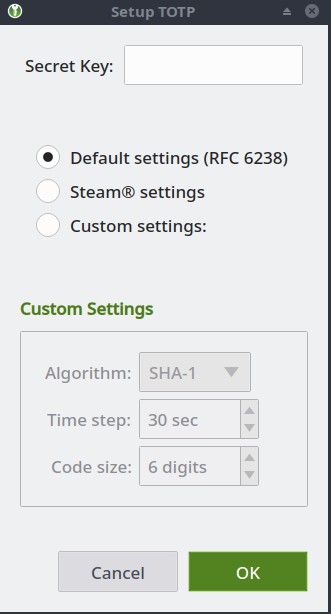
Sometimes 2FA gives you the secret key, sometimes they just give you a QR code. You can use any QR code decoder to get the secret key you need, there's even online ones like https://zxing.org/w/decode.jspx
It will spit out something like this:
Code: Select all
otpauth://totp/SecretKey?secret=JFBVG4R7ORKHEZCFHZFW26L5F55SSP2Y
If you want to port codes from something like Google Authenticator, it can also be done but it's a bit tricky. You need to extract the SQLite database from your phone for the application, and then use something like SQLitebrowser to find the secret keys.
You can also attach arbitrary data to an entry, notes, and so forth. I keep my backup codes here too in notes on the entry. You can also attach files too, but I'm unsure what kind of impact this has on the database size, so I haven't done it.
Yes, this works for the HQ's 2FA. It's what I use for logging in. You can enable HQ 2FA in your User Control Panel.
Also works for Steam, as seen in the screenshot above.






